A network topology refers to the physical or logical layout of a computer network. It defines how devices, such as computers, servers, switches, routers, and other network components, are connected and communicate with each other.
Let us see some networking topologies with the images for better understanding :)
Bus Topology:
All devices are connected to a common communication medium, called a bus.
Each device receives all transmitted data but only processes data intended for itself.
It is relatively simple and inexpensive, but the failure of the main bus can disrupt the entire network.

Star Topology:
All devices are connected to a central device, typically a switch or a hub.
Each device has a dedicated connection to the central device.
If one device fails, only that device is affected, and the rest of the network remains operational.
It provides better performance and scalability than bus topology but relies heavily on the central device.

Ring Topology:
Devices are connected in a circular manner, forming a closed loop.
Each device is connected to two neighboring devices, and data travels in one direction.
It requires less cabling than other topologies, but the failure of one device can disrupt the entire network.
Mesh Topology:
Every device is connected to every other device in the network.
It provides redundant paths, allowing data to be rerouted if one path fails.
It offers high reliability and fault tolerance, but it requires a large number of connections, making it expensive and complex.
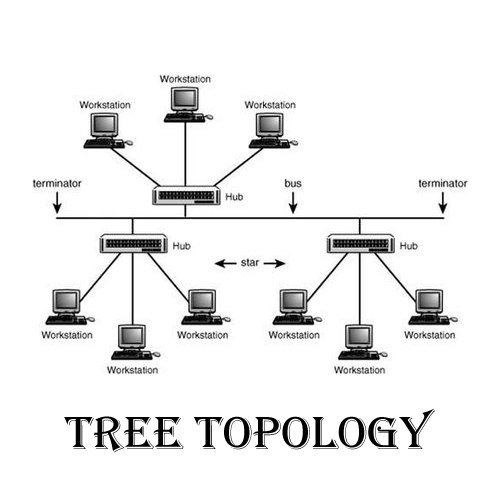
Tree Topology (Hierarchical Topology):
Devices are arranged in a hierarchical structure, similar to a tree.
It combines multiple star topologies connected to a central backbone.
It provides scalability and allows for the segmentation of larger networks into smaller, more manageable subnetworks.
Hybrid Topology:
It combines two or more different network topologies.
For example, a combination of star and mesh topologies can create a star-mesh hybrid network.
NETWORKING DEVICES:
Network Switch:
A network switch is a device that connects multiple devices within a local area network (LAN).
It receives incoming data packets and forwards them to the appropriate destination device based on MAC addresses.
Switches operate at the data link layer (Layer 2) of the OSI model.
They provide high-speed and efficient data transfer between devices.
Router:
A router is a network device that connects multiple networks together, such as LANs or WANs.
It determines the optimal path for data packets to reach their destinations using IP addresses.
Routers operate at the network layer (Layer 3) of the OSI model.
They provide connectivity between different networks and perform functions like routing, forwarding, and network address translation (NAT).
Modem:
A modem (modulator-demodulator) is a device that enables the transmission and reception of data over a communication medium.
It converts digital signals from a computer into analog signals suitable for transmission over telephone lines or other mediums.
Modems are commonly used for connecting to the internet via broadband or dial-up connections.
Network Firewall:
A network firewall is a security device that monitors and controls incoming and outgoing network traffic.
It acts as a barrier between an internal network and external networks (like the internet) to protect against unauthorized access and malicious activities.
Firewalls can enforce security policies, filter network traffic based on protocols or ports, and detect and block potential threats.
Wireless Access Point (WAP):
A wireless access point is a device that allows wireless devices to connect to a wired network.
It enables Wi-Fi connectivity and acts as a central hub for wireless communication within a specific area.
WAPs are commonly used in homes, offices, and public spaces to provide wireless network access.
Network Hub:
A network hub is a simple device that connects multiple Ethernet devices together.
It receives incoming data and broadcasts it to all connected devices.
Hubs operate at the physical layer (Layer 1) of the OSI model and are less commonly used nowadays, as they are inefficient compared to switches.
Network Interface Card (NIC):
A network interface card, also known as a network adapter, is a hardware component that enables a device to connect to a network.
It provides the necessary interface between the device and the network medium, allowing data transmission and reception.
NICs can be built-in (integrated) or added as expansion cards to devices like computers, servers, or printers.
These are some of the key network devices commonly used in computer networks. Each device plays a specific role in facilitating network communication, connectivity, and security.
ROUTING

Routing is the process of determining the optimal path for data packets to reach their destination across multiple networks.
Routers are the network devices responsible for routing. They examine the destination IP address of a packet and make decisions on how to forward it.
Routing protocols, such as OSPF (Open Shortest Path First), EIGRP (Enhanced Interior Gateway Routing Protocol), or BGP (Border Gateway Protocol), are used to exchange routing information and build routing tables.
Routers maintain routing tables, which contain information about network routes and next-hop destinations.
Interior routers handle routing within an autonomous system (AS), while exterior routers handle routing between different ASes.
Routing algorithms consider factors such as cost, network congestion, and link reliability to determine the best path for packet delivery.
Switching:
Switching involves the forwarding of data packets between devices within a local network.
Switches are network devices that operate at the data link layer (Layer 2) of the OSI model.
Ethernet is the most common technology used for switching within LANs.
Switches use MAC (Media Access Control) addresses to identify devices connected to their ports.
When a switch receives a packet, it examines the destination MAC address and forwards the packet only to the port associated with that address.
Switches dynamically learn MAC addresses by observing the source addresses of incoming packets and build forwarding tables.
They use techniques like store-and-forward or cut-through switching to forward packets.
Interaction between Routing and Switching:
Routers handle inter-network routing, determining the path between different networks.
Switches handle intra-network switching, efficiently forwarding packets within a local network.
Typically, routers connect different LANs or WANs, while switches connect devices within a LAN.
In complex networks, routers and switches are interconnected to provide connectivity at different network layers.
Overall, routing and switching are integral components of network infrastructure, ensuring data is correctly routed and delivered to the intended destinations within a network or across multiple networks. They contribute to efficient data transmission, network performance, and connectivity.
Network Security:
Firewalls: Protect networks by filtering and monitoring network traffic to prevent unauthorized access and detect potential threats.
VPN (Virtual Private Network): Establishes secure encrypted connections over public networks, enabling remote access and data privacy.
Intrusion Detection and Prevention Systems (IDPS): Monitor network traffic for signs of potential security breaches or malicious activities
Let s study in detail about network security:
FIREWALL
A firewall refers to a security device or software that acts as a barrier between an internal network and external networks, such as the internet. Its primary function is to monitor and control network traffic based on predetermined rules or policies. Firewalls examine incoming and outgoing data packets to determine whether to allow or block them, based on criteria like source and destination IP addresses, port numbers, and protocols. By enforcing access controls and filtering traffic, firewalls help protect networks from unauthorized access, malicious attacks, and the spread of malware or viruses.
Purpose of Firewalls:
Network Access Control
Traffic Filtering
Network Segmentation
Privacy and Confidentiality
Types of Firewalls:
Network Layer (Packet Filtering) Firewalls
Stateful Inspection Firewalls
Application Layer (Proxy) FirewallsNext-Generation Firewalls (NGFW):
Firewall Rules and Policies:
Access Control Lists (ACLs)
Inbound and Outbound Rules
Default Deny Policy
Firewall Deployment:
Perimeter/Frontend Firewalls: These firewalls are placed at the network boundary, protecting the internal network from external threats.
Internal/Backend Firewalls: These firewalls are deployed internally within the network to provide segmentation and control traffic flow between internal network segments.
Host-Based Firewalls: Software-based firewalls installed on individual devices, such as servers or workstations, to provide an additional layer of protection at the device level.
Firewall Management and Maintenance:
Regular Updates and Patching: Keeping firewall firmware and software up to date with the latest security patches to address vulnerabilities.
Log Monitoring and Analysis: Monitoring and analyzing firewall logs to identify suspicious activity, potential threats, and policy violations.
Rule Optimization: Regularly reviewing and optimizing firewall rules to ensure they align with the organization's security policies and minimize unnecessary access
VPN(Virtual Private Network)
A VPN (Virtual Private Network) is a technology that lets you create a private and secure connection over the internet. It protects your data by encrypting it, making it unreadable to anyone who might try to intercept it.
When you use a VPN, your device connects to a server in a different location. All your internet traffic goes through this server, creating a secure "tunnel" that keeps your data safe. It's like having a private highway for your online activities.

VPNs are commonly used for:
Privacy and Security: VPNs hide your IP address and encrypt your data, making it difficult for others to track your online activities or steal your information.
Accessing Restricted Content: By connecting to a server in a different country, you can access websites and services that are otherwise unavailable in your location. For example, you can watch streaming content from other countries.
Secure Remote Access: VPNs allow you to securely connect to your work network from outside the office, ensuring that your communication and data remain protected.
Public Wi-Fi Protection: When you use public Wi-Fi networks, such as in cafes or airports, VPNs encrypt your data, preventing others from spying on your online interactions.
IDPS (Intrusion Detection and Prevention System)
An IDPS (Intrusion Detection and Prevention System) is a security technology that keeps an eye on network traffic and computer systems to detect and prevent unauthorized access or attacks. It uses different methods to spot suspicious behavior or known attack patterns.
There are two types:
1. network-based (monitors network traffic)
2.host-based (monitors individual systems).
1.IDPS can either detect and alert administrators (IDS) or actively intervene to stop attacks (IPS).
2.When it detects a threat, it sends alerts to administrators, who can take action to protect the network.
3.IDPS works alongside other security tools and requires careful setup to ensure effective performance.
4.Its main goal is to protect computer systems from unauthorized access and potential damage.
THANK YOU FOR READING!
